When performing triage on a Linux system you suspect might be compromised, there are many aspects of the system that you may want to look at. In SANS FOR577, we talk about some existing tools and even writing your own bash script to collect triage data. In a case I worked a year or so ago, the attacker installed an LD_PRELOAD rootkit, which was itself pretty interesting, but one aspect that was a little unusual in this case was that they also set the immutable bit on /etc/ld.so.preload. I’ve used the find command to find suid and guid binaries and scripts, but it is a bit more of a pain to find files with the immutable bit. So, I wrote by a Python script that takes one or more file or directory names and returns the names of any that have the immutable bit. You can also add a switch to search recursively and another to return full path rather than relative (the default). I figured I can’t be the only person who ever needed a tool like this, so I’ve added it to my GitHub script repo.
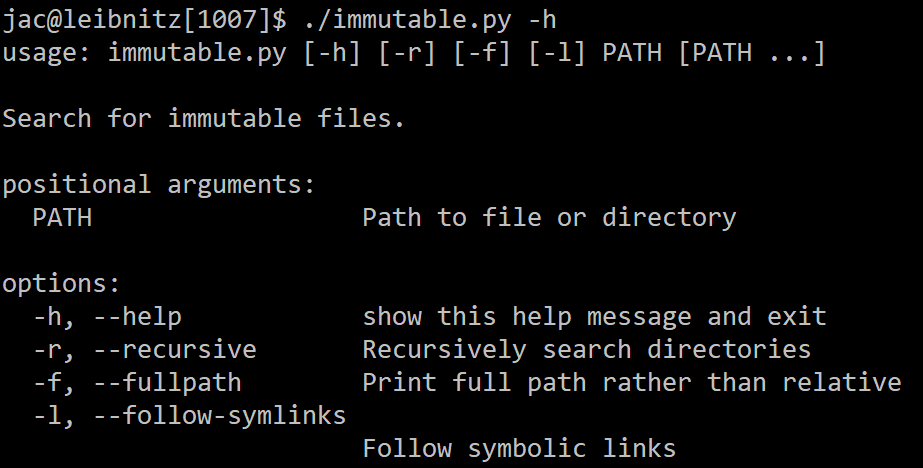
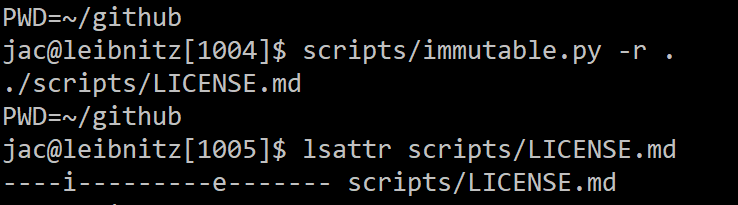
As with all of my tools/scripts, if you have have questions or suggestions you can e-mail me at my address below or on the handlers list.
References:
https://www.sans.org/cyber-security-courses/linux-threat-hunting-incident-response/
https://raw.githubusercontent.com/clausing/scripts/refs/heads/master/immutable.py
https://github.com/clausing/scripts
—————
Jim Clausing, GIAC GSE #26
jclausing –at– isc [dot] sans (dot) edu
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Discover more from Cyber GRC Hive
Subscribe to get the latest posts sent to your email.

