
Explore our 2024 Threat Analysis and 2024 Predictions
In 2024, two key trends defined the cybersecurity landscape: the resilience of cybercriminal networks despite law enforcement actions and the growing complexity of enterprise attack surfaces. In addition, state-sponsored threat actors, primarily linked to China and Russia, intensified their focus on critical infrastructure and leveraged generative AI to conduct influence operations to advance their geopolitical objectives.
Recorded Futures just-released threat report explores these trends and more. It presents the industrys most comprehensive analysis of intelligence from 2024 as well as predictions to prepare your security organization for the year ahead.
Read on for a summary of key topics and themes, and then download the full report for an in-depth look at the adversarys TTPs so you can strengthen your security posture.
Top Themes from our 2024 Research
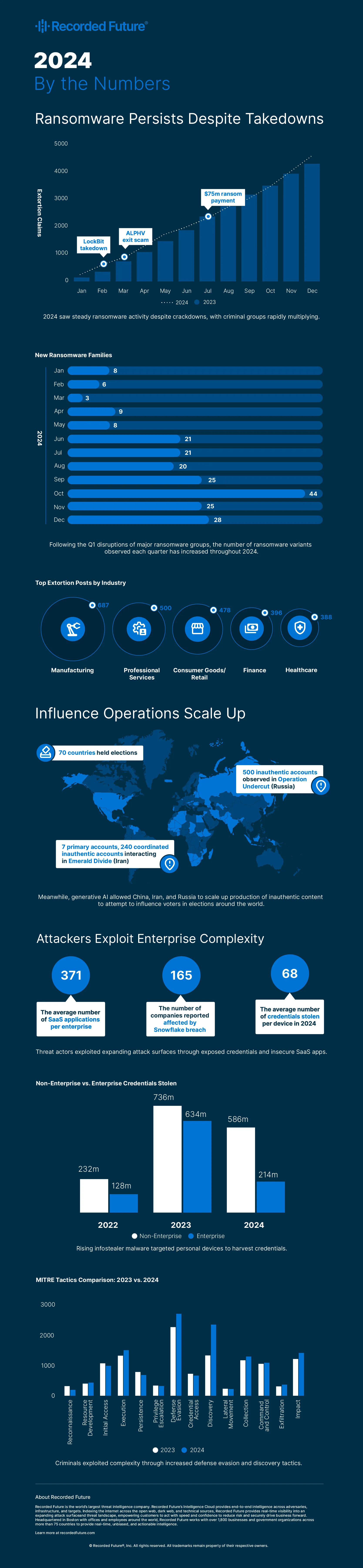
Theme #1: Extortion Groups Proliferated Despite Law Enforcement Action
Despite significant global law enforcement efforts targeting ransomware groups like LockBit and ALPHV, cybercriminals demonstrated their ability to adapt and thrive. They reorganized, leveraged leaked malware builders, and shifted to smaller, independent groups. By mid-2024, ransomware payments had already reached $459.8 million, with a record $75 million paid by a single victim.
Theme #2: Growing Adoption of SaaS Led to More Identity Exploits
Organizations now use an average of 371 SaaS applications, up significantly from 2021, with each application requiring its own access credentials. This increase in SaaS reliance gave threat actors more opportunities to exploit stolen or exposed credentials, which were implicated in high-profile breaches such as those at Snowflake and Change Healthcare. In both cases, attackers used stolen credentials obtained through infostealer malware to bypass single sign-on (SSO) protections.
Theme #3: State-sponsored Influence Operations Escalated
State-sponsored threat actors, including those linked to China, Russia, and Iran, escalated their activities in 2024. These operations targeted critical infrastructure and leveraged generative AI to conduct influence campaigns during key elections.
Chinas Volt Typhoon group pre-positioned itself in US critical infrastructure, raising concerns about its potential for strategically timed cyberattacks. Meanwhile, Russia and Iran used generative AI to accelerate the creation and dissemination of inauthentic content aimed at influencing public opinion and destabilizing democracies worldwide.
Theme #4: Tactics and Techniques Emphasized Defense Evasion
Threat actors increasingly employed advanced tactics to evade detection. Malware targeting macOS and Linux systems surged, reflecting the growing use of these platforms in enterprise environments. Tools like RustDoor and AMOS exploited cross-platform functionality to deliver sophisticated payloads, while ransomware groups targeted critical hypervisors such as VMware ESXi.
Defense evasion techniques, such as reflective code loading and the abuse of remote monitoring tools, became more prevalent. These methods enabled attackers to bypass endpoint detection and response (EDR) solutions.
Top Insikt Group Predictions for 2025
#1: AI Impersonation will be the Next Big Attack Vector for SaaS Applications
Insikt Group expects that a major breach will very likely result from one of two AI-associated factors: implementation of generative AI into enterprise workflows or abuse of AI for effective impersonation. In either case, it is likely that a SaaS application will play a role in initial access or data exposure.
#2: Additional Typhoon Activity will Affect New Sectors
Insikt Group predicts that more high-profile breaches of US critical infrastructure by China-linked APTs will be disclosed in 2025, expanding beyond the energy and telecommunications sectors. These breaches are likely aimed at pre-positioning for disruptive operations.
#3: macOS and Mobile Threats Join Windows and Cloud
Insikt Group forecasts that one of the high-impact cyber incidents of 2025 will likely be associated with either macOS malware or mobile malware. This will result from certain environmental factors reaching breaking points, such as higher attention to macOS targets and increased access to sensitive corporate and financial data via mobile devices.
#4: Crypto Fraud Will Lead to a Market-destabilizing Event
The soaring value of cryptocurrency, as well as an incoming US administration set to pursue crypto-friendly policies, will drive more aggressive and ambitious fraud attempts. Inskit Group predicts that criminals will likely be emboldened by the crypto boom to carry out market-destabilizing scams that will at least temporarily reduce the value of cryptocurrencies and lead to calls to restrict their use.
Get the 2024 Recorded Future Annual Report Today
Download the report to access the complete set of research themes and predictions plus detailed analysis. Then reach out to our team to find out how our threat intelligence solutions and expertise can help your organization prevent attacks and avoid business disruption in 2025.
To read the entire analysis, click here to download the report as a PDF.
Discover more from Cyber GRC Hive
Subscribe to get the latest posts sent to your email.

