What is CVE-2024-50623
CVE-2024-50623 is a critical unrestricted file upload and download vulnerability that could lead to remote code execution (RCE).
What are the affected products?
The vulnerability affects Cleo’s managed file transfer (MFT) products Harmony, VLTrader, and LexiCom before version 5.8.0.21.
- Cleo Harmony 5.8
- Cleo LexiCom 5.5.0.0
- Cleo LexiCom 5.6
- Cleo LexiCom 5.6.1
- Cleo LexiCom 5.6.2
- Cleo LexiCom 5.7
- Cleo LexiCom 5.8
- Cleo VLTrader 5.8
Description
On December 13, 2024, Recorded Futures Insikt Group published a TTP Instance detailing cybersecurity firm watchTowr Labs analysis of an alleged proof-of-concept (PoC) exploit for CVE-2024-50623.
CVE-2024-50623 stems from insufficient input validation, improper path sanitization, and weak license verification logic within the /Synchronization endpoint of the affected Cleo software. The /Synchronization endpoint facilitates file synchronization, transfer, and command-based file operations (read, write, update, delete) between Cleo cluster nodes.
 Login page for dashboard management on an exposed Cleo instance
Login page for dashboard management on an exposed Cleo instance
Insikt Group also published a TTP Instance on December 13, 2024 discussing CVE-2024-55956, a related command injection vulnerability that allows unauthenticated users to run unauthorized commands on a system using Cleos Autorun directory. According to cybersecurity firm Huntress, Cleo’s patch in version 5.8.0.21 failed to fully address CVE-2024-50623; Cleo released version 5.8.0.24 to fix the then-zero day vulnerability, which was later assigned CVE-2024-55956.
Insikt Group also published a TTP Instance on December 13, 2024 discussing CVE-2024-55956, a related command injection vulnerability that allows unauthenticated users to run unauthorized commands on a system using Cleos Autorun directory. According to cybersecurity firm Huntress, Cleo’s patch in version 5.8.0.21 failed to fully address CVE-2024-50623; Cleo released version 5.8.0.24 to fix the then-zero day vulnerability, which was later assigned CVE-2024-55956.
Both CVE-2024-50623 and the related CVE-2024-55956 are listed in the US Cybersecurity and Infrastructure Security Agency (CISA)s Known Exploited Vulnerabilities (KEV) database. Cybersecurity firm GreyNoise also observed malicious hosts looking to exploit the vulnerabilities.
On December 26, 2024, Insikt Group published a TTP Instance detailing the CL0P ransomware group exploiting both CVE-2024-50623 and CVE-2024-55956. At the time of writing, there were 1,618 exposed Cleo instances on Censys and 1,234 on Shodan. However, not all of these are necessarily vulnerable as their specific versions are unknown.
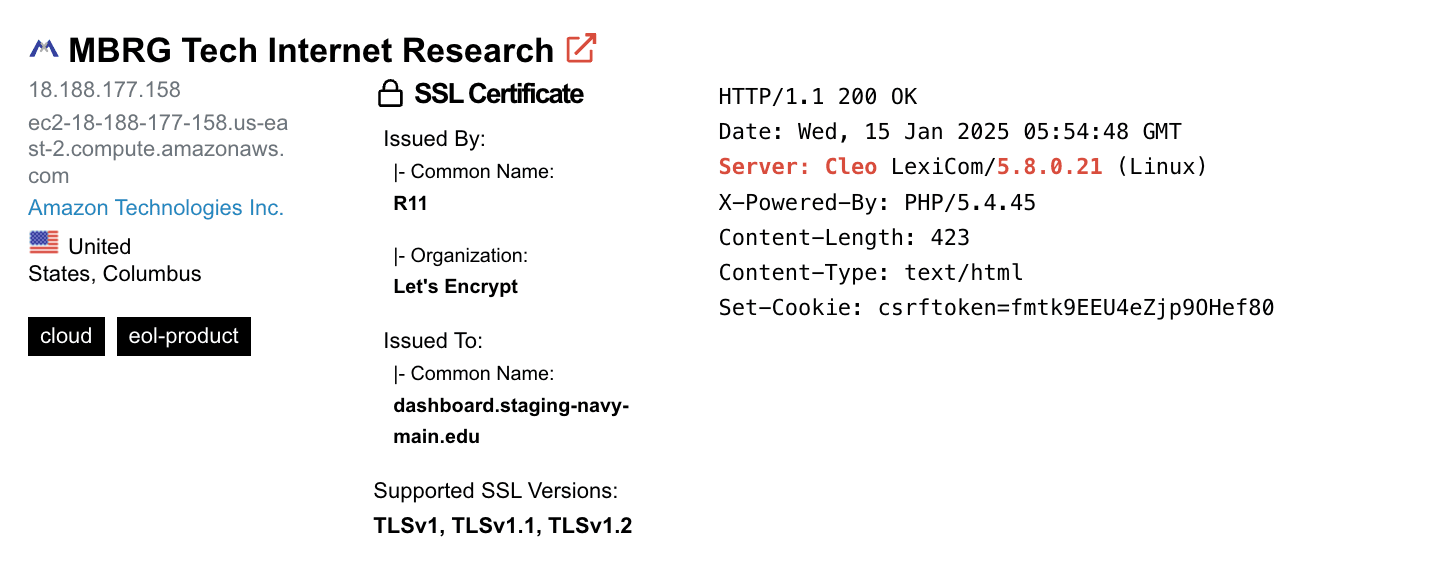 Shodan results exposing specific version numbers, making it easier for threat actors to identify vulnerable instances
Shodan results exposing specific version numbers, making it easier for threat actors to identify vulnerable instances
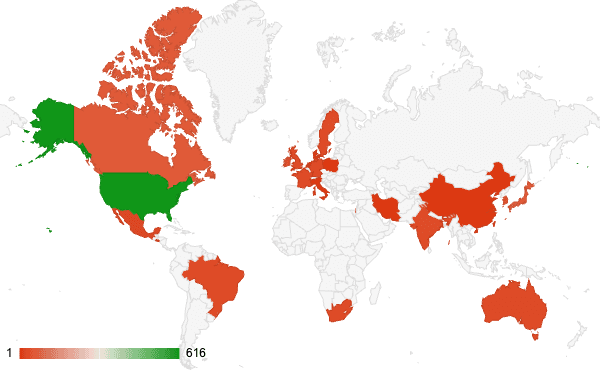 Nearly 50% of exposed instances on Shodan are geolocated in the US
Nearly 50% of exposed instances on Shodan are geolocated in the US
Recommended Actions
Cleo strongly advises all customers to immediately upgrade their instances of Harmony, VLTrader, and LexiCom to the latest released patch (version 5.8.0.21) to address additional discovered potential attack vectors of the vulnerability.
How Recorded Future can Help:
- Attack Surface Intelligence – Identify internet-facing assets vulnerable to CVE-2024-50623.
- Vulnerability Intelligence – Gain helpful context on CVE-2024-50623 to aid in patching and prioritization discussions.
- Insikt Group – Access a Nuclei template created by Insikt Group for CVE-2024-50623 that enables defenders to test potentially vulnerable Cleo instances prior to the patched version.
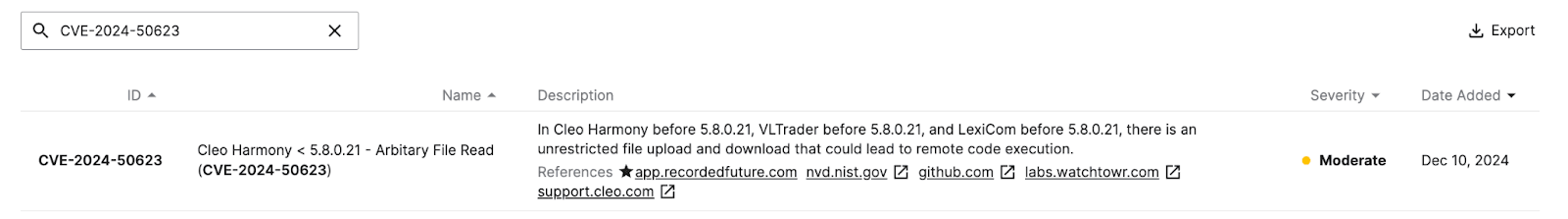 Signature for CVE-2024-50623 in Recorded Future Attack Surface Intelligence
Signature for CVE-2024-50623 in Recorded Future Attack Surface Intelligence
About Insikt Group:Recorded Futures Insikt Group threat research team is comprised of analysts, linguists, and security researchers with deep government and industry experience.
Insikt Group publishes threat intelligence to the Recorded Future analyst community in blog posts and analyst notes
Discover more from Cyber GRC Hive
Subscribe to get the latest posts sent to your email.

