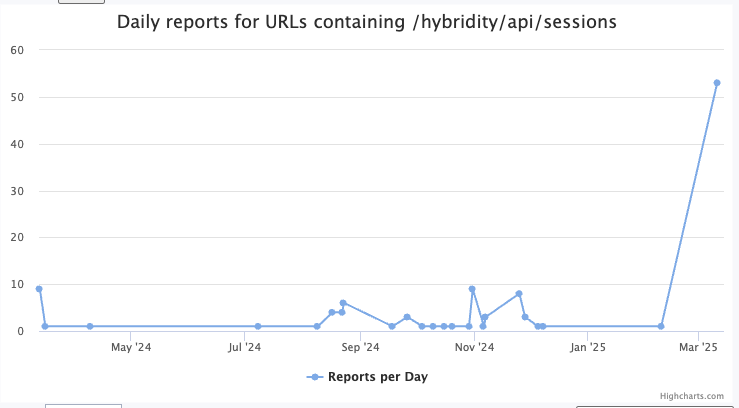
Today, I noticed increased scans for the VMWare Hyprid Cloud Extension (HCX) “sessions” endpoint. These endpoints are sometimes associated with exploit attempts for various VMWare vulnerabilities to determine if the system is running the extensions or to gather additional information to aid exploitation.
The specific URL seen above is
/hybridity/api/sessions
This particular request is likely used to brute force credentials. the “sessions” endpoint expects a JSON payload with the username and payload like:
{
"username": "admin",
"password": "somecomplexpassword"
}
The response will either be a 401 response if the authentication failed or a 200 response if it succeeded. A successful response includes a “sessionId”, which will be used as a bearer token to authenticate additional requests.
So far, we see these requests mostly from one IP address: %%ip:107.173.125.163%% using randomized valid user agents. The IP address was first seen yesterday in our logs, and is scanning for Log4j vulnerable systems and a few other issues. It may also attempt to brute force a few other web applications. For a complete list of requests sent by this IP address, see this page.
—
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Discover more from Cyber GRC Hive
Subscribe to get the latest posts sent to your email.