What is CVE-2025-0994?
CVE-2025-0994 is a high-severity deserialization vulnerability in Trimble Cityworks, an asset management and work order software designed for local governments and utilities. The critical infrastructure sectors Cityworks services include water and wastewater systems, energy, transportation systems, government services and facilities, and communications.
The vulnerability affects Cityworks versions before 15.8.9 and Cityworks with Office Companion versions before 23.10.
Successfully exploiting CVE-2025-0994 can allow authenticated attackers to conduct remote code execution (RCE) against a targets Microsoft Internet Information Services (IIS) web server.
 Figure 1: Login page on an exposed Cityworks instance (Source: Recorded Future)
Figure 1: Login page on an exposed Cityworks instance (Source: Recorded Future)
Insikt Groups Assessment of CVE-2025-0994
Indicators of compromise (IoCs) shared by Trimble suggest that the vulnerability is being exploited to deliver custom Rust-based loaders capable of loading VShell and Cobalt Strike into memory. Additionally, the threat actors delivered an obfuscated JavaScript payload located in the %TEMP% folder, two unknown files, three malicious executables with randomized, alphanumeric filenames (for example, fq1u4t83[.]exe), and two files masquerading as legitimate services (winpty.dll and winpty-agent[.]exe).
The malicious files were likely downloaded into the victim’s environment from threat actor-controlled Cobalt Strike C2 servers.
Based on the IoCs shared by Trimble, the threat actors used 192.210.239[.]172:3219 and 192.210.239[.]172:4219 as staging infrastructure. Insikt Group has validated this IP address as a C2 server for Cobalt Strike.
There is insufficient evidence to definitively confirm which files were transferred from the threat actors infrastructure; however, the obfuscated alphanumeric-named executables stored in the Temp folder or the JavaScript payload are two possibilities.
At the time of writing, there were 111 exposed Cityworks instances on Shodan, 21% of which are vulnerable based on identified version numbers. The majority of exposed instances are also geolocated in the US and include multiple .gov domains.
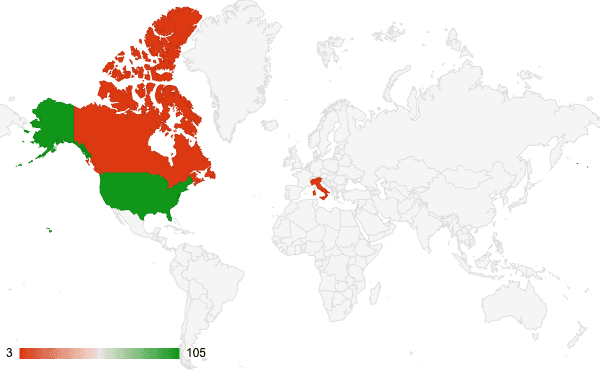
Figure 2: Nearly 95% of exposed Cityworks instances on Shodan are geolocated in the US (Sources: Shodan, Recorded Future)
Trimble shared the following list of IoCs related to their observed exploitation of CVE-2025-0994:
| IoC | Type | Description |
| 4b7561e27c87a1895446d7f2b83e2d9fcf71e6d6e8bc99d44818dc39a6ff99d5 | SHA-256 | Obfuscated JavaScript payload |
| 4ffc33bdc8527a2e8cb87e49cdc16c3b1480dfc135e507d552f581a67d1850a9 | SHA-256 | VShell loader |
| 8a6c735f3608719ec9f46d9c6c5fc196db8c97065957c218b98733a491edd899 | SHA-256 | Unknown |
| 883d849b94238c26c57c0595ccb95b8c356628887b9a3628bf56e726332af925 | SHA-256 | Cobalt Strike loader |
| 151a71c43e63db802d41d5d715aa98eb1b236e0a6441076a8d30fd93990416b4 | SHA-256 | Unknown |
| 1de72c03927bcd2810ce98205ff871ef1ebf4344fba187e126e50caa1e43250b | SHA-256 | Cobalt Strike loader |
| 14a072113baa0a1e1e2b6044068c7bc972ae5e541a0aec06577b0d6663140079 | SHA-256 | Unknown malicious file fq1u4t83[.]exe |
| 04dc3a16e1e2b4924943805a1cea5e402c4f2304c717ea21fdf43274b8c34a84 | SHA-256 | Unknown malicious file q0pe6x96[.]exe |
| f09b51b759dfe7de06fa724bd89592f5b8eae57053d5fb4891e40f24055103fb | SHA-256 | Unknown malicious file szm9wz8m[.]exe |
| C:windowstempz1[.]exe | File path | Malicious binary download path |
| C:windowstempz2[.]exe | File path | Malicious binary download path |
| C:windowstempz44[.]exe | File path | Malicious binary download path |
| C:windowstempz55[.]exe | File path | Malicious binary download path |
| C:WindowsTempUDGEZR[.]exe | File path | Malicious binary download path |
| C:WindowsTempz55.exe_winptywinpty-agent[.]exe | File path | PUTTY binary download path |
| C:WindowsTempz55.exe_winptywinpty[.]dll | File path | PUTTY binary download path |
| 192.210.239[.]172:3219 | IPv4:port | Staging IP address |
| 192.210.239[.]172:4219 | IPv4:port | Staging IP address |
| 23.247.136[.]238 | IPv4 | Threat actor-controlled IP address |
| 31.59.70[.]13 | IPv4 | Threat actor-controlled IP address |
| 31.59.70[.]11 | IPv4 | Threat actor-controlled IP address |
| 149.112.117[.]49 | IPv4 | Threat actor-controlled IP address |
| 192.210.137[.]81 | IPv4 | Threat actor-controlled IP address |
| 192.210.183[.]118 | IPv4 | Threat actor-controlled IP address |
| cdn.phototagx[.]com | Domain | Threat actor-controlled callback domain |
| ifode[.]xyz | Domain | Threat actor-controlled domain |
| https[:]//cdn.lgaircon[.]xyz[:]443/jquery-3.3.1.min.js | URI | Cobalt Strike C2 |
| https[:]//192.210.239[.]172/messages/73KWf-o0-s0hxVCDJp1sfAHRcgdm7 | URI | Cobalt Strike C2 |
Table 1: IoCs shared by Trimble related to their observed exploitation of CVE-2025-0994 (Source: Trimble)
Recommended Actions
Organizations should upgrade to Cityworks version 15.8.9 or later, and Cityworks with Office Companion version 23.10 or later. CISA has included this CVE in their Known Exploited Vulnerabilities Catalog, recommending immediate mitigation actions or discontinuation of the product if mitigations are unavailable. Given its active exploitation and high severity rating, organizations should prioritize patching this vulnerability to safeguard your company’s assets from potential attacks.
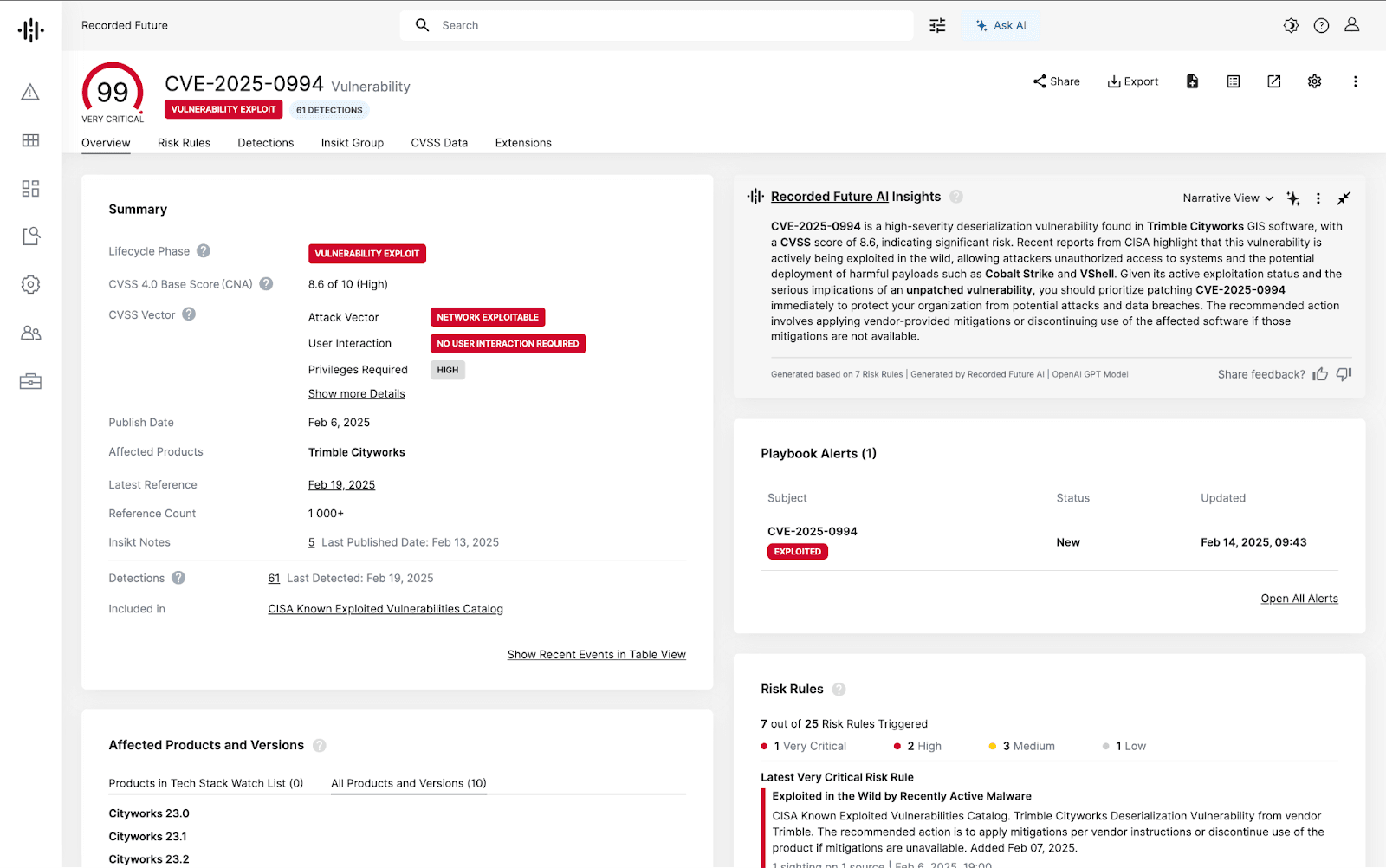
Figure 3: Vulnerability Intelligence Card for CVE-2025-0994 in Recorded Future (Source: Recorded Future)
How Recorded Future Can Help:
- Insikt Group – Download the attached YAML file in this blog post to access a Nuclei template created by Insikt Group for CVE-2025-0994 that enables defenders to test potentially vulnerable Trimble Cityworks instances prior to the patched version.
- Attack Surface Intelligence – Identify internet-facing assets vulnerable to CVE-2025-0994.
- Vulnerability Intelligence – Gain helpful context on CVE-2025-0994. to aid in patching and prioritization discussions.
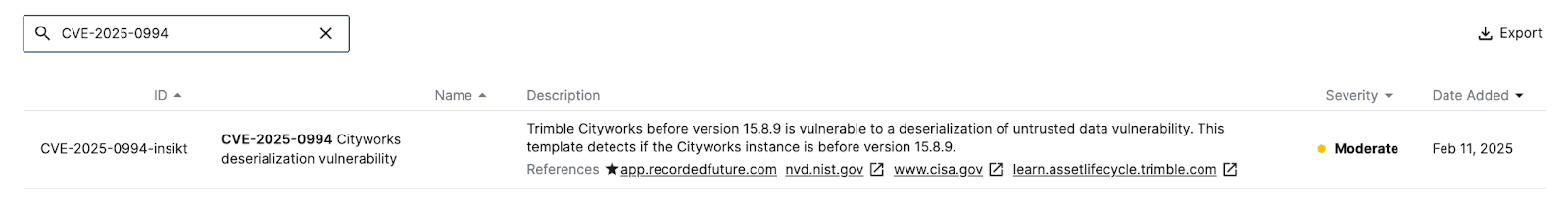 Figure 4: Signature for CVE-2025-0994 in Recorded Future Attack Surface Intelligence (Source: Recorded Future)
Figure 4: Signature for CVE-2025-0994 in Recorded Future Attack Surface Intelligence (Source: Recorded Future)
About Insikt Group:
Recorded Futures Insikt Group threat research team is comprised of analysts, linguists, and security researchers with deep government and industry experience.
Insikt Group publishes threat intelligence to the Recorded Future analyst community in blog posts and analyst notes.
Discover more from Cyber GRC Hive
Subscribe to get the latest posts sent to your email.

