- Solutions
- Services
- COBIT 5
- Digital Forensic Investigations & Data Recovery
- Endpoint Detection & Response (EDR) Services
- Enterprise Gap Analysis
- Enterprise Risk Management & Audit
- Enterprise Technology Audit
- Firewall Solutions
- HITRUST
- IDS-IPS Solutions & Services
- Infosec Team Setup Services
- ISO 27001
- ISO 27001 Assessment and Certification Services
- Logs Management & Monitoring
- NIST 800
- PCI DSS Readiness Self-Assessment and Certification
- Pen Test/Red Team Setup Services
- Security and Posture Management Services
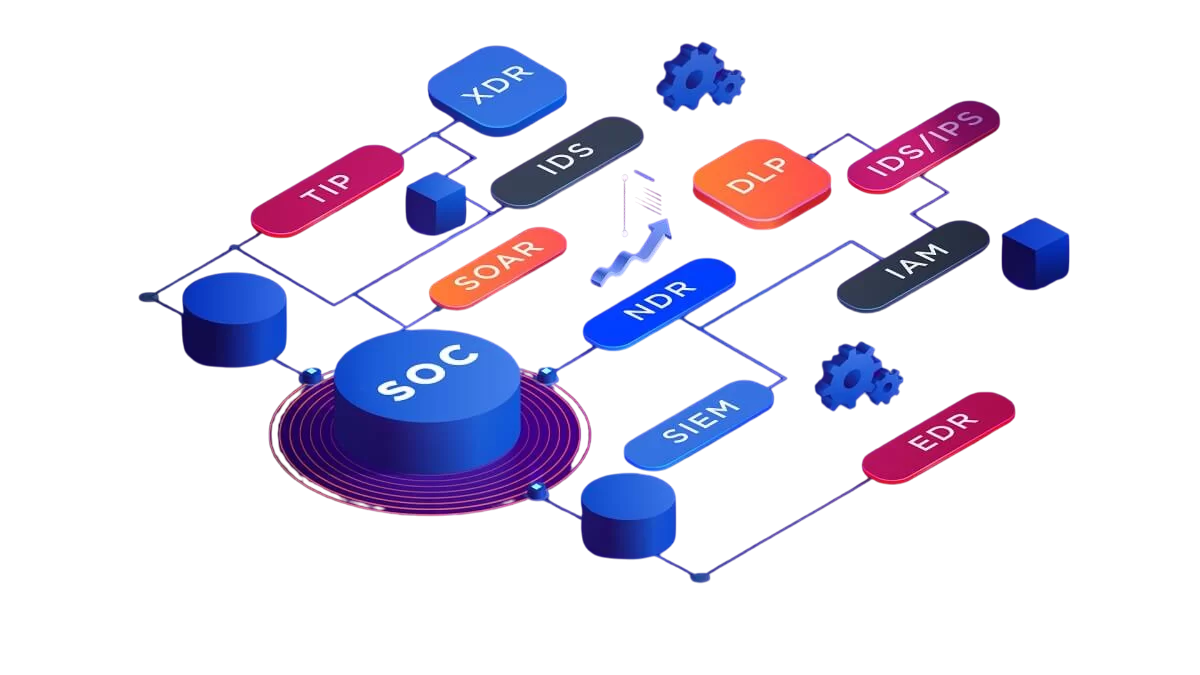
- Security Operation Center (SOC) Team Setup & Services
- SWIFT (CSP & CSCF) Assessment and Readiness
- XDR/SIEM Services
- GRC
- AI
- Company
- Resources
- Insights
Loading...
Next-Gen SOC-as-a-Service, Built for Scale and Expertise
Security Operation Center (SOC) Team Setup
How We Deliver
At Cyber GRC Hive (CGH), we deliver state-of-the-art Security Operations Center (SOC) solutions that embody industry best practices for cybersecurity defense. Our SOC services operate around the clock, utilizing sophisticated tools and methodologies such as behavior analytics, threat intelligence, and incident forensics to monitor, detect, and respond to cyber threats in real time.
- Proven track record of success
- Customized solutions tailored to your needs
- Dedicated support team available 24/7
- Commitment to innovation and excellence

0+
Team Member
Solution
Safeguarding Your Digital Assets with Advanced Solutions
Cyber GRC Hive
Our team of cybersecurity experts is skilled in leveraging automation and orchestration to enhance response times and accuracy, significantly reducing the risk of potential breaches. We integrate these technologies with a layered defense strategy that includes endpoint detection, network security, and cloud-based protections, ensuring comprehensive coverage across all your critical assets.
With CGH’s SOC services, your business benefits from a proactive cybersecurity environment that not only detects and mitigates threats swiftly but also adapts and evolves with the cybersecurity landscape. This proactive approach ensures that your enterprise remains resilient against advanced threats, minimizing downtime and maintaining operational continuity.

Managed SOC & XDR
Around-the-clock, US-based Security Operations Center (SOC) staffed by expert cybersecurity professionals. Advanced XDR (Extended Detection and Response) platform delivers a comprehensive security solution, leveraging AI and automation to accelerate incident response.
Penetration Testing & Reporting
Comprehensive testing to identify vulnerabilities and prevent unauthorized access. Ensures strict identity and access management by applying least privilege principles to protect sensitive data and systems.

Incident Response Management
Get instant alerts for suspicious activity both on and off your network.
Expert team follows a structured incident response plan to quickly contain threats, minimize impact, and restore operations.
Centralized Log Management
Unified log storage for easier security analysis and compliance reporting.
Fully managed security operations with 24/7 monitoring, alerting, and incident response—backed by a team of expert cybersecurity professionals.
Need Help?
Frequently Asked Question
What is an MSP in Cybersecurity?
An MSP (Managed Service Provider) is a third-party company that remotely manages a business’s IT infrastructure and systems. In cybersecurity, MSPs specialize in securing networks, applications, and data through continuous monitoring, threat detection, and expert support.
They help businesses offload IT responsibilities, boost efficiency, and ensure strong, ongoing cyber protection.
What Is Included in Our Cybersecurity Services?
Cybersecurity services encompass a range of tools and practices to protect systems and data from cyber threats. Core components include:
Threat Intelligence – Tracking and analyzing emerging threats.
Risk Management – Identifying and addressing IT security risks.
Data Protection – Safeguarding sensitive information.
Access Control – Regulating user access to systems and data.
Firewall Management – Blocking unauthorized network traffic.
Incident Response – Handling and recovering from breaches.
Cybersecurity Training – Educating employees on safe practices.
Compliance Management – Meeting regulatory and industry standards.
Vulnerability Assessment – Detecting and fixing security gaps.
Managed Security Services – Outsourcing security tasks to experts.
Who Benefits from Cybersecurity Services & Management?
Cybersecurity is essential for all organizations, but some industries face higher risks due to the sensitive data they handle. Key sectors that benefit the most include:
Finance – A prime target for cybercriminals due to financial data.
Healthcare – Holds confidential patient records, often targeted for ransomware.
Legal – Manages sensitive client information and legal documents.
Government & Public Sector – Protects citizen data and critical infrastructure.
Manufacturing – Faces threats to operations and supply chains.
Retail – Vulnerable to credit card and personal data breaches.
Construction – Often hit by ransomware and phishing scams.
Marketing & Media – At risk of DDoS and politically motivated attacks.
Logistics – Exposed to threats that can disrupt global operations.
Technology – Frequently targeted for valuable IP and infrastructure data.
Higher Education – Holds sensitive student and research information.
Contact Us
Ready to protect your business with a flexible security solution?

